Eng
Eng
- Home Appliances, Tools and Household Goods
- Consumer Goods & Electronics
- Products & Solutions for Enterprises
- Toys & Goods for Kids
- All vendors
- Home Appliances, Tools and Household Goods
- Consumer Goods & Electronics
- Products & Solutions for Enterprises
- Toys & Goods for Kids
- Blowers
- Lawn mowers
- Garden shredders
- Cultivators and motoblocks
- High-pressure cleaners
- Chain saws
- Accessories for irrigation and high pressure cleaners
- Pumps
- Shears for garden
- Sprayers
- Shovels
- Garden tools
- Garden furniture
- Garden fencing
- Potbelly stoves
- Trolleys for garden construction
- Tenty i zavisy
- Goods for picnic
- Accessories for lawn mowers and trimmers
- Accessories for chainsaws
- Wood splitters
- UPS and accessories
- Sources of uninterruptible power supply
- Gaming products
- Gaming PCs and hardware
- Processors for gaming
- Game consoles and accessories
- Virtual reality glasses
- Gaming peripherals and accessories
- Glasses for computer
- Games
- Game collectible figurines and accessories
- Merchandise, gaming attributes
- Computer peripherals
- Computer components
- Media tablets
- Monitors
- Drives and Flash-memory
- Laptops & Accessories
- PC and All-in-One PC
- Software
- Accessories and options for computer and office electronics
- Cleaners
- 2E Custom PC
- Computer tables
- Travel goods
- Cooler bags, thermoboxes
- Gas cylinders and accessories
- Haberdashery
- Umbrellas
- Tactical gear and equipment
- Radio equipment and navigation
- Tactical watches
- Accessories for tactical drones
- Tactical equipment
- Pouches
- Military gloves
- Knee and elbow pads
- Plate carriers
- Elements for plate carriers
- Tactical vests
- Tactical flask
- Tactical eye protection
- Tactical glasses
- Tactical goggless
- Personal heating equipment
- Chemical heating
- Electric heating
- Hearing protection
- Active Shooting Headphones and Headsets
- Navushnyky ta harnitury striletski pasyvni
- Tactical shovels
- Backpacks, bags, duffle-bags
- Tactical backpacks
- Backpacks, bags, duffle-bags
- Sling bags
- Camping equipment
- Karrimat and mattresses
- Tactical clothing and footwear
- Raincoats
- Chemical light
- Bicycle accessories
- CCTV Cameras
- Smart switches and buttons
- Smart Sensors
- Smart controllers, gateways, panels
- Smart sockets, relays and motors
- Smart drives, thermostats, control panels
- Smart sirens
- Search engines
- Heating systems
- Towel warmers
- Radiators
- Pipe fittings
- Accessories for radiators and heated towel rails
- Accessories and components for hot water heating
- Circulation pumps
- Underfloor heating hydronic
- Underfloor heating
- Underfloor heating pipes
- Intercom systems
- Thermoregulators
- Sewer pipes and fittings
- Accessories and mounts for alarm systems
- Accessories for temperature controllers
- Accessories for thermotechnics
- Control automation for thermotechnics
- Quick installation systems
- Network filters
- Light source, Lights
- Accessories for lamps
- Chandeliers, lamps, sconces, floor lamps
- Electric light bulbs
- Light fixtures
- Fixtures external
- Indoor (interior) light fixtures
- Fitting and light accessories
- Electrical-installation equipment
- Sockets and switches
- Electrical switchboards
- Contactors
- Terminals
- Automatic switches
- Circuit breakers
- Voltage Limiters
- Relays and alarms
- Tires
- Modular and change-over switches
- Kits and accessories for smart lighting
- Clockwork toys
- Toys-keychains
- Toys
- Bath toys
- Toys for sand
- Playing Kits
- Toy transport
- Toy weapons
- Game Figures and Accessories
- Construction sets
- Dolls
- Puppet show
- Doll accessories
- Baby mobiles
- Musical instruments
- Stuffed Toys
- Balls
- Board games
- Puzzles
- Вeanbag
- Radio-controlled cars
- Learning toys
- Creativity
- Goods for holidays
- Music and storage boxes
Unbreakable keyboard. Why not to trust what you see in movies

What happens in movies or TV shows may never happen in real life. When it comes to breaking-in, robbery or hacking, movies can show completely unrealistic scenarios.
For example, viewers believe that some powder can detect the infrared rays protecting the Grail cup. Or someone believe that a criminal can connect a wire to the Ajax keyboard, read the password and hack the security system. That is why we will analyze perhaps the most popular crime in movies – hacking the security system through the keyboard.
Typically, it is performed in three stages:
- Keyboard search;
- Obtaining physical access or radio signal interception;
- Hacking the system through third-party software.
Let's figure out what's wrong at each of these stages.
Step 1: Search for a keyboard
The first step in any attempted intrusion is to gather information. When criminals enter a building, they know in advance which direction to go and where to look for devices to hack.
To determine the exact location of the wired keyboard, the criminal must use a powerful multi-scanner to find the desired cable in the wall. However, the multi-scanner does not determine which cable is found – doorbell, intercom or electrical wiring.
If the keyboard is wireless, looking for hidden cables won't help. Criminals can scan the radio signal to determine the location of a wireless device. However, the data exchange between the device and the hub using TDMA technology is allocated a small time slot. The rest of the time, their communication modules are inactive. It would take the criminal tens of minutes to determine the source of the signal. And even then, there are no guarantees that the detected signal source belongs to the exact device it needs. Also, it may not be an Ajax device, because other devices also use Ajax frequencies.
However, to capture radio signals, criminals use a code-grabber. This is a special device for intercepting the signal transmitted during the system is armed or disarmed. But hacking an Ajax device in this way is impossible due to signal encryption and a proprietary communication protocol.
Protection technologies:
- block encryption with a floating key;
- TDMA principle.
Step 2: Physical access
To attack a security system, criminals always look for physical access to the device.
As a rule, keyboards are installed at the entrance to the premises. Usually these are load-bearing walls made of brick, concrete or reinforced concrete with a thickness of 25 cm or more (depending on building standards and regulations). Sometimes the thickness can reach up to 50 cm, and it is impossible to drill such a wall silently in a few seconds.
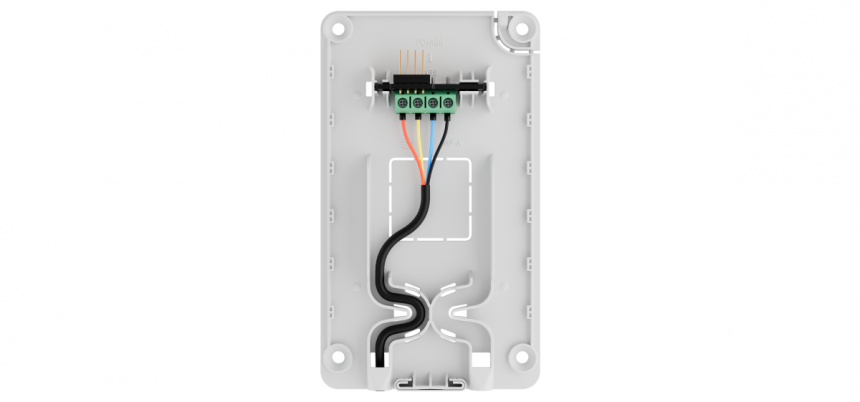
In addition to attracting the attention of the neighbors, there is a risk of damaging the device with a drill. The line of the wired keyboard Fibra is routed through the cable channel in the SmartBracket mounting panel. These channels have a curved design, and the cable is fixed with ties. Therefore, if criminals drill into the SmartBracket, they will likely cut all the wires.
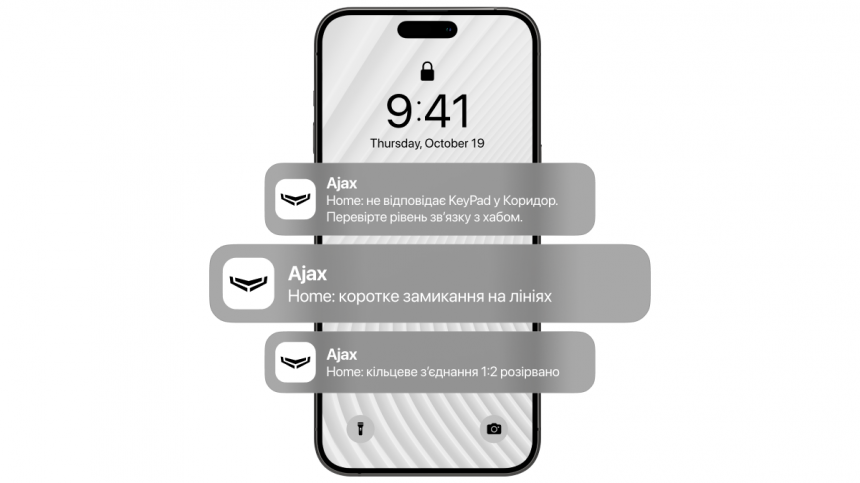
In addition to damaging the device, users and the security control panel (PSC) will be notified of the intrusion attempt. In case of cable damage, they will receive a notification about a short circuit and a broken ring connection (if using a "ring" topology). If the cable is broken or the keyboard is damaged, a notification will also be sent about the loss of communication with the hub.
Even if a criminal tries to damage the security system using electrical sabotage (such as a stun gun), LineProtect Fibra will absorb the shock. All devices between LineProtect and the hub will continue to operate.
LineProtect Fibra is a module for protecting Ajax hubs and wired devices from sabotage, when a criminal arranges a short circuit, supplies voltage of 110/230 V~ or uses stun gun shocks. The module monitors the input and output voltage on the Fibra line. If LineProtect detects an abnormal voltage on the line, it activates the circuit breakers and disconnects power to the devices controlled by the hub.
Wireless keyboards have no wires at all. Furthermore, there are no wires inside the casings of Ajax wireless and even wired keyboards. Therefore, it is absolutely impossible to connect to any wire inside the device's casing. The only available wire is the insulated and hidden Fibra cable.
Some criminals detach the keyboard from the wall and break it, resulting in a system failure. However, the keyboard is just a part of the system, not its "brain". Therefore, damaging the keyboard does not pose a significant threat to the overall security system. In addition, Ajax keyboards have a tamper that notifies users and Central Monitoring Station (CMS) in case of opening the case of the device, removing the device from the mounting panel or tearing it from the surface.
Protection technologies:
- instant notification;
- loss of communication detection;
- tamper alarm;
- LineProtect Fibra;
- ring connection.
Step 3: Hack
Let's assume that the criminal connected to the keyboard and remained undetected by the system. However, connecting to just one wire, as shown in movies or TV shows, is meaningless, because the Fibra line has four wires: two signal and two power.
Fibra uses floating key encryption to protect data. Data hacking and accessing requires the power of a supercomputer and weeks or even years of wasted time. In other words, it's a waste. However, even encrypted data needs to be retrieved first. Each communication session between the hub and the device begins with authentication: unique markers and properties are compared. If at least one parameter fails the check, the hub ignores the device's commands. Therefore, falsifying or intercepting data makes no sense.
The keyboard does not store user codes, which makes it impossible to guess them. When a user enters a code, it is sent to the hub in encrypted form, and the hub verifies it. The codes inside the hub are securely stored in a hashed form, in addition, the Ajax hub uses the OS Malevich real-time operating system, providing viruses and cyber-attacks protection.
It is also impossible to guess the code using a brute-force attack. If an incorrect code is entered three times in a row or an unverified access device is used within a minute, the keypad will be locked for the time specified in the settings. During this time, the hub will ignore all codes and access devices, informing security system users and the Central Monitoring Station (CMS) about the unauthorized access attempt.
Ultimately, it's impossible to hack the system unnoticed. Any attempt to remove the system from protection is detected, and users and the Central Monitoring Station (CMS) receive notifications.
Protection technologies:
- encrypted proprietary communication protocol;
- substitution protection;
- automatic blocking from unauthorized access.
Conclusions
Hacking an Ajax system is a difficult challenge. Data is protected by encryption, and the keyboard does not store codes. The hub verifies every command, filtering out unauthorized access attempts. Traditional brute-force attacks are prevented by the keypad's auto-lock feature.
What happens in movies, TV shows, or commercials is subject to the laws of drama, often deviating from the principles of physics and mathematics. Try to be skeptical about everything you see in the movies.